
A Security Operations (SecOps) Solution, bringing together Endpoint Management, IT Service Management & Security.
Book a DemoOverview
IT Security and Operations teams are faced with the monumental task of staying one step ahead of the ever-evolving threat landscape.
When a threat becomes evident, teams must prioritize and roll out preventative and remediation tasks at scale across a diverse endpoint estate; all while continuously monitoring and reporting their threat posture. Organizations must be able to see AND control Endpoints, Operations and Security, whether located on-premises or in the cloud, regardless of location, connection type or status.
Comply With Privacy Laws
Using a single platform, automate the complex deadlines and regulations related to GDPR, LGPD, CPRA, and hundreds of other regulations.
Remove Manual Tasks
Automate robotic automation and automated data discovery to completely automate manual request fulfilment chores.
Satisfy All Request Types
Automate all requests—for access or deletion - from customers or staff members on a single platform.
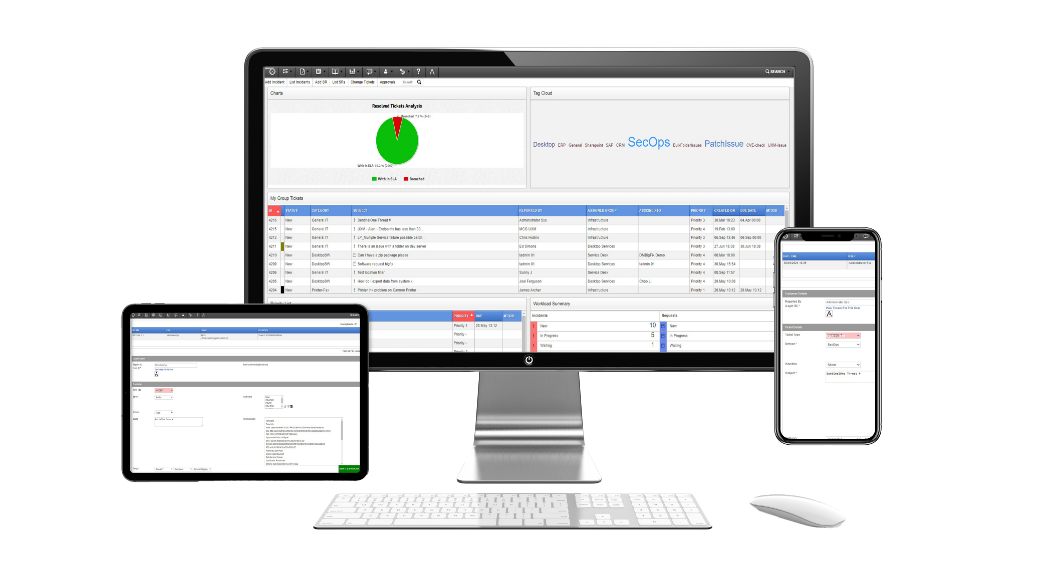
Manage Endpoints
Efficiently control, secure, and monitor all endpoint devices across the organization.
Reduce Risk
Proactively identify, mitigate, and manage potential threats and vulnerabilities to minimize security risks.
Deliver Patch Management
Automate timely distribution of software updates and security patches to maintain system integrity.
Heighten Security Posture
Strengthen overall security measures, defenses, and protocols to protect against cyber threats.
Effectively Collaborate
Enhance team communication, coordination, and workflow efficiency with collaborative tools and platforms.
Orchestrate & Automate
Streamline and automate IT processes, reducing manual effort and improving efficiency.
Improve Productivity
Increase operational efficiency and performance, enabling better use of resources and time.
Leverage AI
Utilize artificial intelligence for advanced analytics, threat detection, and decision-making support.
Enforce Compliance
Ensure consistent adherence to regulatory standards, policies, and industry best practices.
Manage Inventory
Accurately track, control, and optimize IT assets and resources.
Reduce Cost
Lower operational expenses through efficient resource management and process optimization.
Keeping your current ITSM investments, you can also enhance your ITSM operations to the next generation of SecOps, by leveraging the full suite of Security solutions (SIEM, SOAR, UEBA).
InvictaONE SecOps therefore takes you from the world of ITSM, to the new world of fully integrated SecOps, Automation and AIOps
Book a Demo
We work closely with industry leading solutions providers to create certified technology integrations that are best of breed, end-to-end IT Service Management solutions.
Book a Demo
Explore our other Products
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.

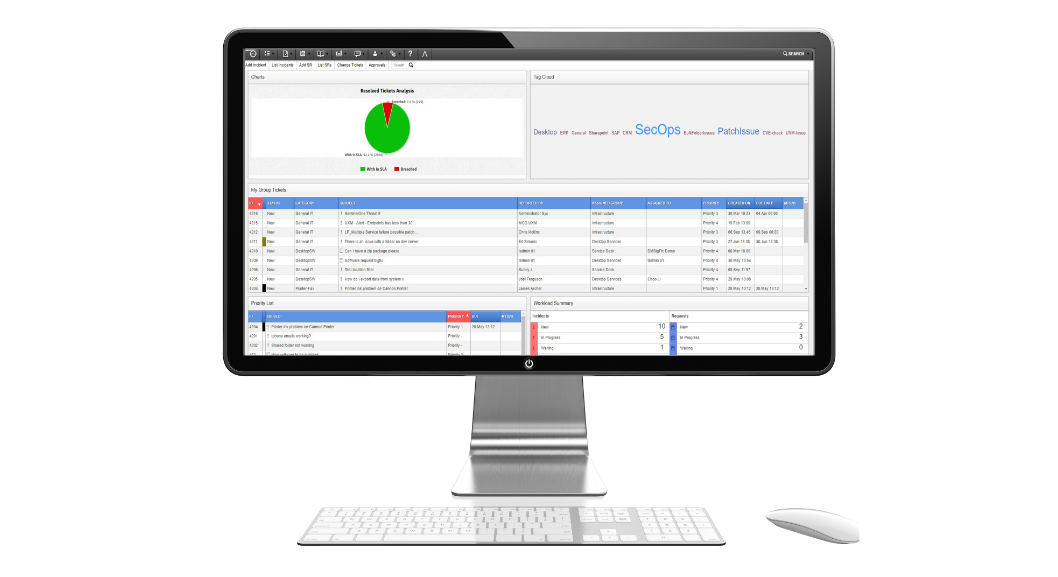
A centralised point of contact for users to seek help, request services, report incidents, raise queries related to IT services or any other organizational functions.

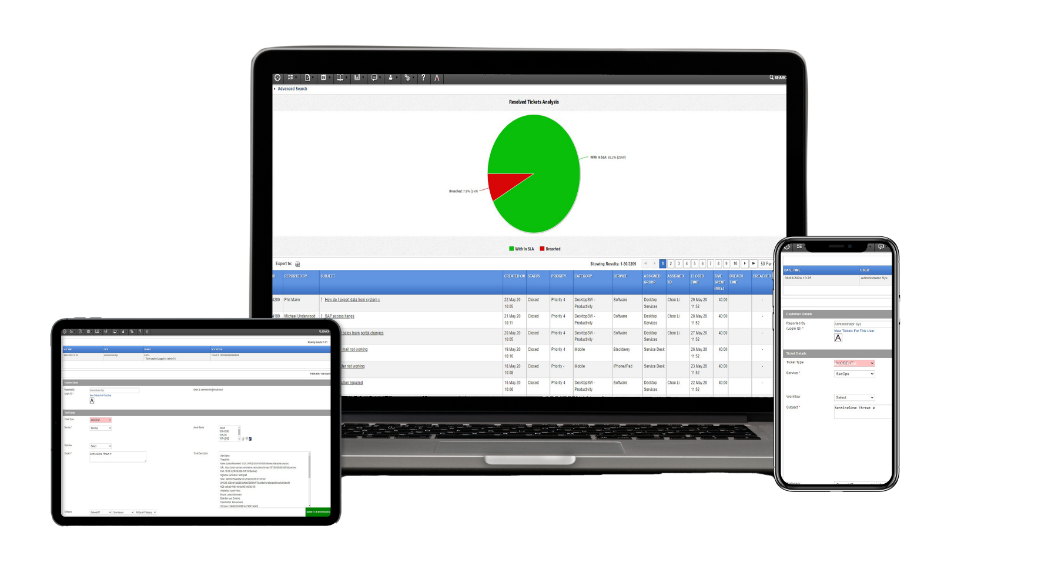
Providing a tailored solution designed for modern schools, channeling queries to the right department or individual, streamlining resolutions.